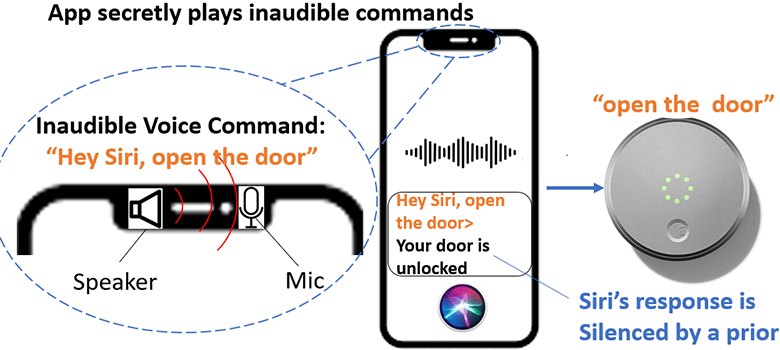
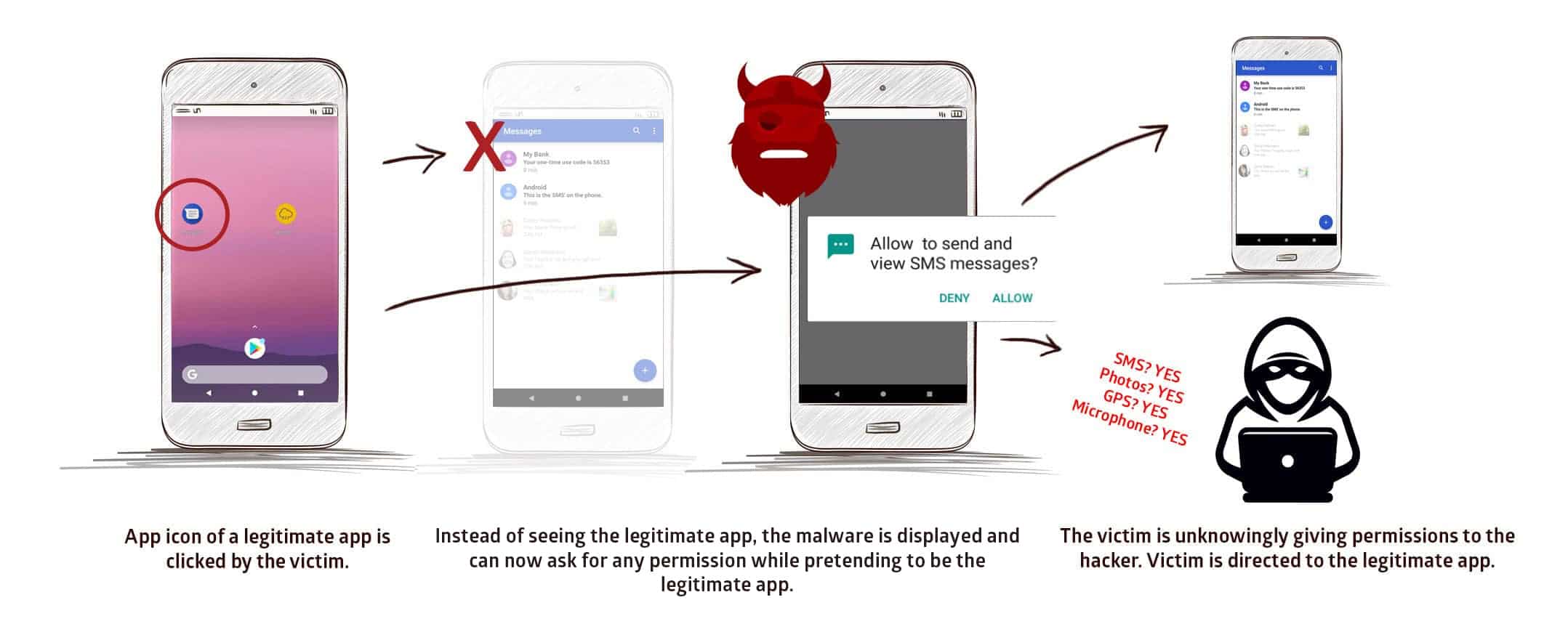
Can an iPhone be hacked? A breakdown of common hacks and cyber hygiene best practices | McKelvey School of Engineering at Washington University in St. Louis

Zero-Click' hacks are growing in popularity. There's practically no way to stop them | Technology News,The Indian Express